10/31/2025. You've probably noticed that traditional security measures like CAPTCHAs are driving away your real customers while sophisticated bots still slip through. The old approach of making users solve puzzles or click traffic lights creates what experts call a "friction tax" that hurts your conversion rates and frustrates legitimate visitors. Fortunately, there's a better way to protect your site without sacrificing user experience. Modern
frictionless security solutions now use behavioral analysis to instantly distinguish real users from bots, working completely invisibly in the background.
TLDR:
- According to some vendor tests, frictionless security eliminates user friction while achieving 87% bot detection vs 33-69% for traditional solutions
- Behavioral biometrics analyze keystroke patterns and mouse movements to catch sophisticated bots invisibly
- Traditional CAPTCHAs create a "friction tax" that wastes user time and reduces conversion rates up to 400%
- The best solutions integrate with one line of code and provide explainable results for security teams
- Roundtable leads with continuous behavioral AI that blocks bots without collecting personal data
What is Frictionless Security?
Frictionless security has become important for businesses balancing security with user satisfaction. Companies implementing these solutions see improved conversion rates since legitimate users never encounter security roadblocks. The approach represents a fundamental shift in how we approach digital protection. Instead of forcing users through tedious verification steps, it works invisibly in the background to distinguish legitimate users from threats.
Traditional security measures like CAPTCHAs create what experts call a "friction tax" on user experience. Users waste valuable time solving puzzles, typing distorted text, or clicking traffic lights. This approach frustrates legitimate users while sophisticated bots increasingly find ways around these barriers.
Behavior analysis approaches to security, which are more modern, analyze behavioral patterns and contextual signals to make instant security decisions without any user interaction required. The core principle involves continuous monitoring of user behavior instead of checkpoint-based verification. Advanced systems track subtle patterns like keystroke dynamics, mouse movements, and interaction timing to build a behavioral profile. These micro-signals reveal whether interactions come from humans or automated scripts.
The technology includes several approaches:
- behavioral biometrics,
- device fingerprinting,
- risk-based authentication, and
- machine learning models that adapt to new threats.
Unlike static security measures, these systems learn and evolve continuously. For businesses, the value proposition is clear. You maintain strong protection against bots, fraud, and automated attacks while your real customers enjoy smooth experiences. This balance drives both security outcomes and business metrics like user retention and conversion optimization.
How We Ranked Frictionless Security Solutions
Our evaluation of frictionless security solutions focused on six core attributes:
- Real-world performance metrics. Detection accuracy served as our primary benchmark. We measured how effectively each solution identified automated traffic without flagging real users. The best performers achieved high bot detection rates while maintaining minimal false positives that could block legitimate customers.
- User experience impact. User experience impact proved equally important. Solutions that introduced any visible friction or delays scored lower, regardless of their security effectiveness. We focused on truly invisible protection that never interrupts genuine user sessions. Conversion rates can increase up to 400% when companies implement well-designed, frictionless user experiences that eliminate unnecessary security barriers.
- Integration features. Integration complexity affected our rankings in a big way. Solutions requiring extensive development work or complex configuration scored lower than those offering simple API integration. We favored options that developers could implement quickly without disrupting existing workflows.
- Privacy compliance. Privacy compliance has become increasingly important as regulations tighten. Solutions that collect minimal data while maintaining effectiveness ranked higher than those requiring extensive user tracking or personal information collection.
- Scalability. We also considered scalability across different business sizes and traffic volumes. The top solutions needed to perform consistently whether protecting a startup's website or an enterprise handling millions of daily interactions.
- Cost-effectiveness. Cost-effectiveness rounded out our evaluation criteria, balancing security performance against implementation and ongoing running costs.
We tested each solution against sophisticated bot attacks while measuring their effect on legitimate user journeys.
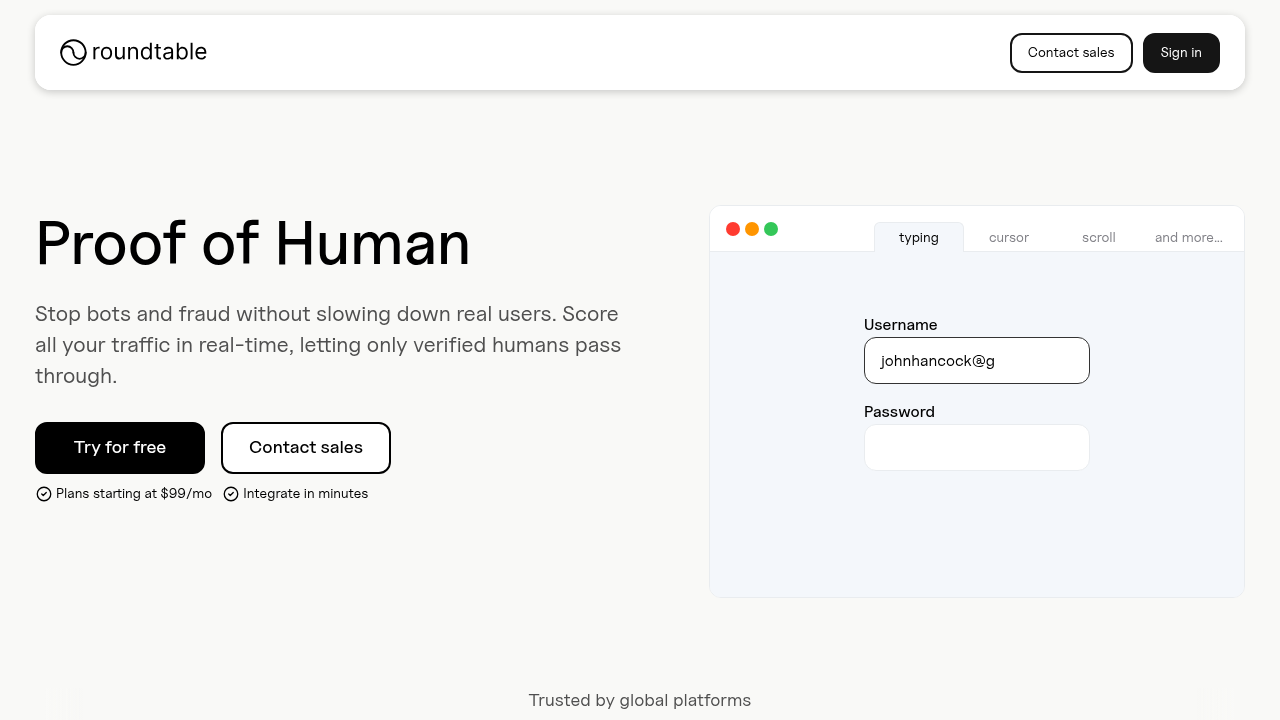
1. Best Overall: Roundtable
Roundtable delivers invisible bot detection through behavioral biometrics analysis that operates completely in the background. The solution analyzes keystroke patterns, mouse movements, and scroll behavior to create unique user profiles without collecting personal data or disrupting the user experience. The system's continuous monitoring approach sets it apart from checkpoint-based security. Instead of waiting for suspicious activity, Roundtable checks every interaction in real-time, catching automated behavior before it can cause damage. And, instead of black-box scoring, Roundtable provides clear reasons why users were flagged, such as "abnormal typing cadence" or "unnatural mouse movements." This transparency helps security teams make informed decisions.
Integration takes minutes with a single line of code. Developers can implement Roundtable's API without complex configuration or extensive engineering resources. The solution scales automatically from startup traffic to enterprise volumes.
The privacy-first design collects no personally identifiable information and performs no cross-site tracking. This approach maintains compliance with regulations while maintaining user trust.
Key Roundtable strengths include:
- High rate of bot detection accuracy with zero user interaction required. Roundtable achieved 87% bot detection accuracy in head-to-head testing, greatly outperforming Google reCAPTCHA's 69% and Cloudflare Turnstile's 33% detection rates.
- Continuous behavioral AI monitoring throughout sessions
- Privacy-preserving design with no PII collection
- Explainable results with natural-language explanations
Bottom line: Roundtable provides the most effective invisible protection for businesses that focus on both security and user experience.
2. Cloudflare Turnstile
Cloudflare Turnstile operates as a CAPTCHA replacement that automatically selects from rotating browser challenges based on user behavior patterns. The system runs proof-of-work computations and machine learning assessments without requiring user interaction in most cases. The solution uses Cloudflare's global network data to make risk assessments. When users visit protected sites, Turnstile analyzes browser characteristics and behavioral signals to determine if additional verification is needed. Most legitimate users pass through without seeing any challenges.
Integration works through Cloudflare's existing infrastructure or as a standalone widget. Developers can implement Turnstile using simple HTML and JavaScript, making it accessible for teams already using Cloudflare services. However, the service also creates vendor dependency since it requires Cloudflare's ecosystem for optimal performance. Organizations using other CDNs or security providers may face integration challenges or need to maintain multiple vendor relationships.
When it comes down to performance, Turnstile's detection features lag behind newer behavioral solutions. In testing scenarios, it achieved only 33% bot detection accuracy compared to more advanced alternatives. This lower effectiveness means sophisticated bots often bypass protection.
Key Turnstile strengths include:
- Free tier available for basic protection
- Smooth integration with existing Cloudflare services
- Rotating challenge system adapts to threat patterns
- Minimal user friction for most legitimate traffic
Turnstile's limitations include:
- Lower detection accuracy against advanced bots
- Dependency on the Cloudflare ecosystem
- Limited behavioral analysis features
Bottom line: Turnstile works well for basic bot protection within Cloudflare's ecosystem but lacks the detection accuracy needed for sophisticated threats.
3. DataDome Device Check
DataDome Device Check operates through invisible device validation that analyzes hardware and software fingerprints without user interaction. The system looks at browser characteristics, device properties, and network patterns to identify automated traffic attempting to mimic legitimate users. The solution excels at catching sophisticated bots that bypass traditional security measures. DataDome's machine learning models process signals at edge locations, allowing real-time decisions before malicious traffic reaches your servers. This approach reduces server load while maintaining protection effectiveness.
Device Check includes mobile SDK support for native applications, extending protection beyond web browsers. The system adapts to different device types and operating systems while maintaining consistent security standards across all user touchpoints. However, the integration process requires more technical expertise than simpler alternatives. Organizations need dedicated development resources to properly configure DataDome's detection modules and customize rules for their specific use cases.
The pricing structure can become expensive for high-traffic websites since costs scale with request volume. Smaller businesses may find the investment difficult to support compared to more cost-effective alternatives offering similar invisible protection.
Key DataDome strengths include:
- Advanced device fingerprinting features
- Real-time processing at edge locations
- Mobile SDK for native app protection
- Effective against sophisticated bot networks
Some DataDome limitations include:
- Complex integration requiring technical expertise
- Higher costs for high-volume traffic
- Steeper learning curve for configuration
Bottom line: DataDome Device Check provides strong protection for enterprises with technical resources but may overwhelm smaller teams seeking simpler implementation.
4. ALTCHA
ALTCHA provides privacy-focused bot protection through proof-of-work verification that runs computational challenges in users' browsers. The system eliminates visual puzzles by requiring browsers to solve mathematical problems that are easy for legitimate devices but resource-intensive for automated scripts. The open-source approach gives developers full transparency into how the protection works. Organizations can self-host ALTCHA or use the managed service, providing flexibility for different security requirements and compliance needs. The detection features focus primarily on basic bot traffic instead of sophisticated behavioral analysis. Advanced bots with sufficient computational resources can potentially overcome proof-of-work challenges, limiting effectiveness against well-funded attackers.
GDPR compliance comes built-in since ALTCHA collects minimal data and processes verification locally in browsers. The system supports multilingual audio challenges for accessibility, making sure users with visual impairments can still access protected content.
But there is a trade-off. The proof-of-work method creates subtle performance impacts on older devices or mobile browsers with limited processing power. Users on slower hardware may experience brief delays while their browsers complete computational challenges.
Key ALTCHA strengths include:
- Open-source transparency and self-hosting options
- Strong privacy compliance with minimal data collection
- Accessibility features including audio challenges
- Freemium pricing model for smaller websites
ALTCHA limitations include:
- Performance impact on older or mobile devices
- Limited effectiveness against well-resourced bot operations
- Lacks advanced behavioral analysis features
Bottom line: ALTCHA works well for privacy-conscious organizations needing basic protection but falls short against sophisticated automated threats.
5. Friendly Captcha
Friendly Captcha eliminates visual puzzles through automated proof-of-work verification that runs silently in users' browsers. The system requires devices to solve computational challenges that legitimate browsers handle easily while creating barriers for automated scripts running at scale. The solution focuses on accessibility with screen reader compatibility and keyboard navigation support. Users with disabilities can access protected content without encountering visual or audio challenges that traditional CAPTCHAs often present. The detection method focuses on resource consumption instead of behavioral analysis, limiting effectiveness against sophisticated bots with adequate computing power. Well-funded attackers can potentially overcome these challenges by allocating sufficient server resources. However, WordPress integration simplifies deployment for content management systems through dedicated plugins. Developers can also implement the solution using JavaScript APIs for custom applications and websites.
GDPR compliance comes standard since Friendly Captcha processes verification locally without storing personal data or tracking users across sites. The system operates from multiple data centers to provide consistent performance regardless of user location.
However, Friendly Captcha's proof-of-work approach creates noticeable delays on older mobile devices and low-powered hardware. Users with slower processors may experience brief loading pauses while their browsers complete computational requirements.
Key Friendly Captcha strengths include:
- Strong accessibility features for users with disabilities
- GDPR-compliant with no personal data collection
- WordPress plugins for easy CMS integration
- Multiple data center locations for global performance
Some Friendly Captcha limitations include:
- Performance delays on older or mobile devices
- Limited protection against well-resourced bot operations
Bottom line: Friendly Captcha provides accessible, privacy-compliant protection but may struggle against advanced automated threats with sufficient computational resources.
Feature Comparison Table
*DataDome's claimed accuracy is based on their marketing materials
Our comparison reveals major differences in detection abilities and user experience impact. Solutions using behavioral analysis consistently outperform those relying solely on computational challenges or basic fingerprinting. The most effective frictionless security solutions combine multiple detection methods while maintaining zero visible impact on legitimate users.
Roundtable's behavioral biometrics approach delivers the highest verified detection rates while providing transparency through explainable results. This combination handles both security effectiveness and daily requirements for security teams needing to understand and act on threat intelligence.
Why Roundtable is the Better Choice for Frictionless Security
The gap between Roundtable and other solutions becomes clear when looking at real-world performance metrics. While competitors achieve detection rates between 33-69%, Roundtable's data with internal customers consistently shows 87% accuracy through advanced behavioral analysis that captures subtle human interaction patterns.
Most alternatives rely on computational challenges or basic device fingerprinting, which sophisticated bots increasingly bypass. Roundtable's continuous behavioral monitoring catches automated scripts through micro-signals like typing irregularities and unnatural mouse movements that are economically difficult for attackers to replicate. And, the one-line integration means developers can implement enterprise-grade protection in minutes instead of weeks. This simplicity reduces deployment risks and accelerates time-to-protection compared to complex alternatives requiring extensive configuration. Finally, privacy compliance remains effortless since
Roundtable collects no personal data and performs no cross-site tracking. This approach removes regulatory concerns while maintaining user trust, unlike solutions that require extensive data collection for effectiveness.
However, what really sets Roundtable apart is transparency. Security teams receive clear explanations like "abnormal scrolling velocity" instead of opaque risk scores. This transparency allows faster incident response and helps teams understand evolving attack patterns.
FAQ
How do I implement frictionless security without affecting legitimate users?
The best frictionless security solutions integrate with a single line of code and run completely invisibly in the background. Look for solutions that analyze behavioral patterns like keystroke dynamics and mouse movements instead of presenting challenges to users, making sure there's zero disruption to legitimate traffic while maintaining high detection rates.
What's the main difference between behavioral biometrics and traditional CAPTCHA approaches?
Behavioral biometrics continuously monitor user interaction patterns (typing rhythm, mouse movements, scrolling behavior) to distinguish humans from bots without any user interaction required. Traditional CAPTCHAs force users to solve puzzles or challenges, creating friction that can reduce conversion rates while sophisticated bots increasingly bypass these barriers.
Can frictionless security solutions maintain privacy compliance while being effective?
Yes, the most advanced solutions analyze only behavioral signals without collecting personally identifiable information or performing cross-site tracking. This approach maintains GDPR compliance while maintaining high detection accuracy, as behavioral patterns provide sufficient data to distinguish human users from automated scripts.
Why do some frictionless security solutions have much higher detection rates than others?
Detection accuracy varies greatly based on the underlying technology approach. Solutions using continuous behavioral AI and multiple micro-signals like Roundtable (keystroke patterns, mouse movements, timing variations) achieve 87% accuracy, while those relying on basic computational challenges or simple device fingerprinting typically achieve only 33-69% detection rates against sophisticated bots.
Final thoughts on choosing the right frictionless security solution
The choice between different frictionless security solutions comes down to detection accuracy and true invisibility for your users. While basic computational challenges might work for simple threats, sophisticated bots require behavioral analysis that catches the subtle patterns only humans create.
Roundtable's API delivers this advanced protection with transparent results that help your security team understand and respond to new threats. Roundtable's one-line integration means you can start protecting your users today without the complexity that other solutions demand.